
Our business involves advanced knowledge and technology and so do our customers; therefore, protecting the privacy of our customers and maintaining a highly secured information environment are the cornerstones for securing our long-term competitiveness and sustainable operation.
With the development of information technology and smart manufacturing, modern enterprises extensively utilize information systems. In order to maintain corporate governance and reduce operational risks, we established the “Intangible Asset Security Committee” in 2015, where the heads of legal affairs, information, human resources and other units would carry out crossdepartmental communications and coordinate the planning of the Group's information security policy, information security risk management framework, specific action plans and resources required.
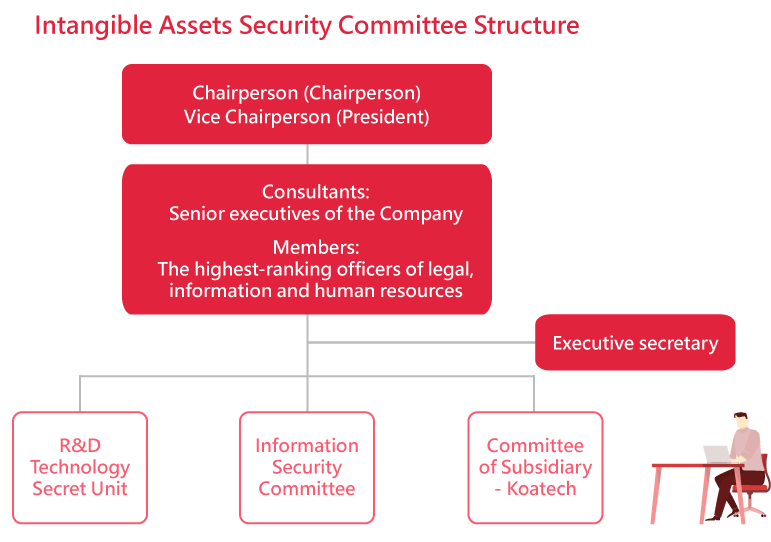
As a R&D-oriented company, Taiflex engages in numerous collaborative projects and exchanges with customers. Therefore, effective management of information security risks and protection of trade secrets are measures to protect customer privacy. The Company has taken one step further and established the Information Security and Knowledge Management Division in March 2022 for the planning, implementation, and risk management of policies related to information security and trade secret protection. The CISO along with the Information Security Officer report to the Board on information security issues and the effectiveness of relevant governance every year.
Information security risk exists in every corner of business operations and involves daily business of each department. Therefore, we require 100% of our employees to sign the Employment and Service Commitment for them to be fully informed of their confidentiality obligations when they join the Company. Upon termination of employment, employees shall return information acquired during the employment and fully comply with the confidentiality obligations.
In order to build an information security culture within the Company, we have monthly promotion of CIPP and conduct annual assessment on the Taiflex confidential information protection standards to ensure all employees of the Company and its subsidiaries are aware of relevant standards. We also encourage employees to use the information security hotline: (07)813-9989#70110/e-mail: IT_security@taiflex.com.tw to report potential information security hazards immediately.
The Company has implemented management measures in eight major aspects to minimize information security risks and achieve the goal of protecting customer privacy. In 2023, the Company did not identify any major cyberattacks or security breaches, nor was there any actual or potential issues which may have material adverse impact on the Company's operation.
The Company has introduced ISO 27001 Information Security Management Systems (ISO 27001:2013) in 2016 and been certified by external agencies for eight consecutive years, building the best security defense for the Company. The CISO is expected to lead the Information Security team to complete the transition to ISO 27001:2022 in 2024. With an effective information security management system, we ensure that all our information systems and digital assets can continue to operate in an environment that maintains confidentiality, integrity, and availability
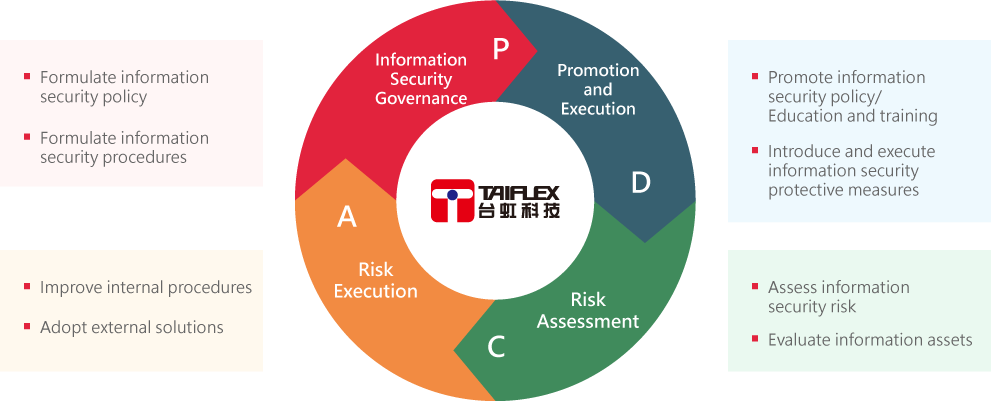
The Intangible Assets Security Committee has established an information security management framework with predictive capabilities and responsiveness. It regularly conducts the iterative process of PDCA to review the effectiveness of various information security operations within the Company. It continuously strengthens various information operation management mechanisms to ensure proper protection of our data and intellectual property, and prevent the theft of trade secrets by malicious individuals, thereby strengthening our competitive advantage to maximize the interests of our customers, shareholders and employees.
A former employee of Taiflex was involved in a criminal case related to the violation of trade secret in 2021. The case was brought to trial in 2022 after the conclusion of investigations by prosecutors, and transferred to the criminal court of the Intellectual Property and Commercial Court in 2024. In view of the violation, our management measures are adjusted as follows: